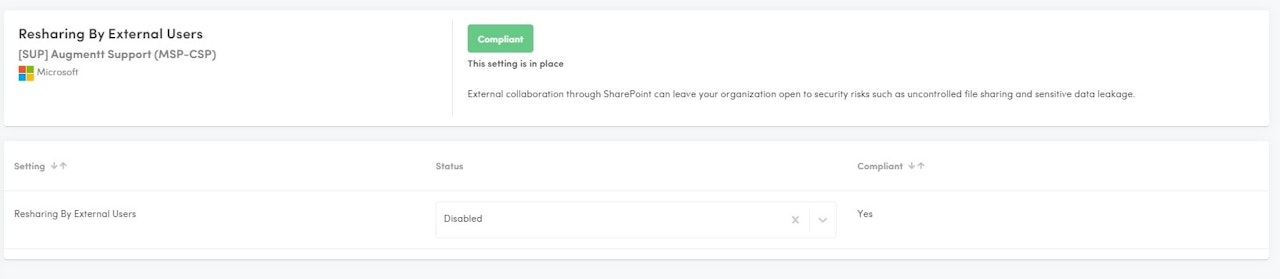

Resharing by External Users
Description: This check verifies that Resharing of files by External Users is disabled.
Why: External collaboration through SharePoint can leave your organization open to security risks such as uncontrolled file sharing and sensitive data leakage.
Configured: Resharing by External users is disabled.
Not Configured: Resharing by External users is enabled.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: No

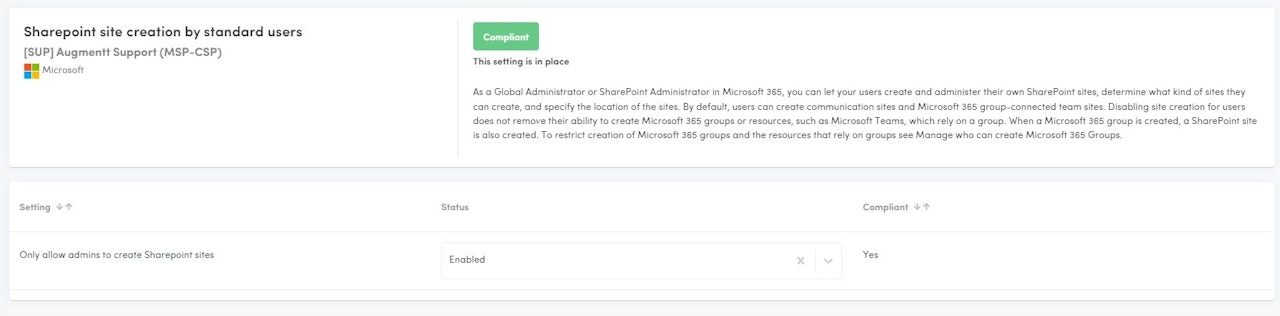
Sharepoint Site Creation by Standard Users
Description: This check verifies if Sharepoint sites could be created by standard users.
Why: As a Global Administrator or SharePoint Administrator in Microsoft 365, you can let your users create and administer their own SharePoint sites, determine what kind of sites they can create, and specify the location of the sites. By default, users can create communication sites and Microsoft 365 group-connected team sites. Disabling site creation for users does not remove their ability to create Microsoft 365 groups or resources, such as Microsoft Teams, which rely on a group. When a Microsoft 365 group is created, a SharePoint site is also created. To restrict creation of Microsoft 365 groups and the resources that rely on groups see Manage who can create Microsoft 365 Groups.
Configured: Users cannot create Sharepoint sites.
Not Configured: Users can create Sharepoint sites.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: No

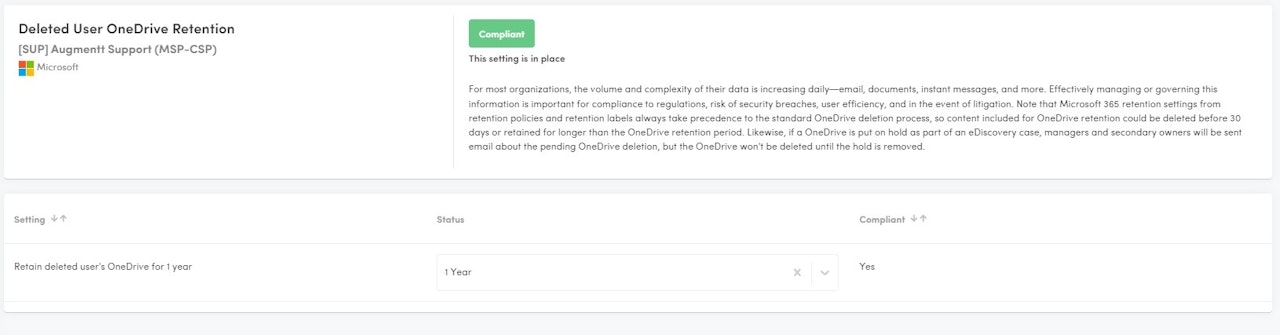
Deleted Users OneDrive Retention
Description: This check verifies that Deleted User's OneDrive Retention settings are extended to 1 year.
Why: For most organizations, the volume and complexity of their data is increasing daily—email, documents, instant messages, and more. Effectively managing or governing this information is important for compliance to regulations, risk of security breaches, user efficiency, and in the event of litigation. Note that Microsoft 365 retention settings from retention policies and retention labels always take precedence to the standard OneDrive deletion process, so content included for OneDrive retention could be deleted before 30 days or retained for longer than the OneDrive retention period. Likewise, if a OneDrive is put on hold as part of an eDiscovery case, managers and secondary owners will be sent email about the pending OneDrive deletion, but the OneDrive won't be deleted until the hold is removed.
Configured: Deleted user's OneDrive is retained for 1 year.
Not Configured: Deleted User's OneDrive is retained for less than 1 year.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: No

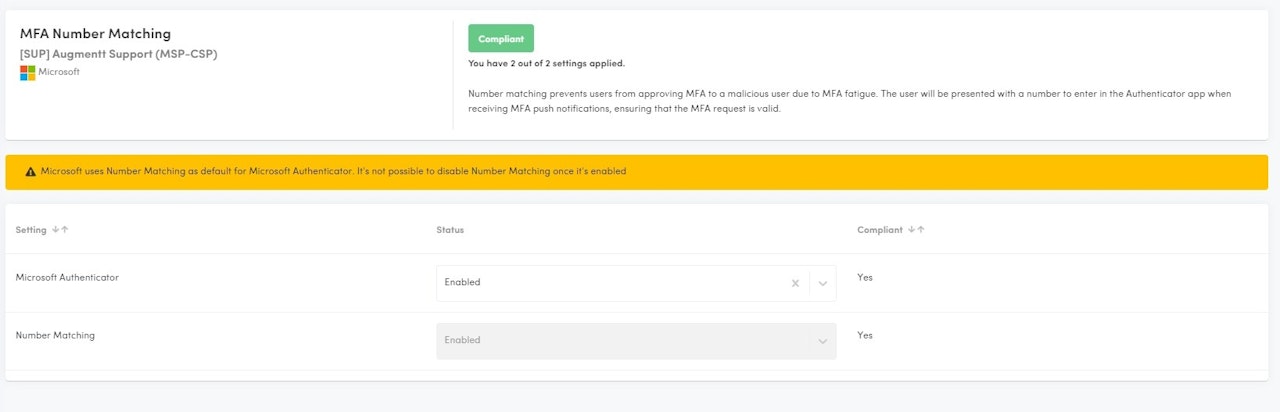
MFA Number Matching
Description: This check verifies that MFA Number Matching is enabled. This requires the Microsoft Authenticator app to be enabled/used.
Why: Number matching prevents users from approving MFA to a malicious user due to MFA fatigue. The user will be presented with a number to enter in the Authenticator app when receiving MFA push notifications, ensuring that the MFA request is valid.
Configured: Number matching is enabled.
Not Configured: Number matching is disabled.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: No

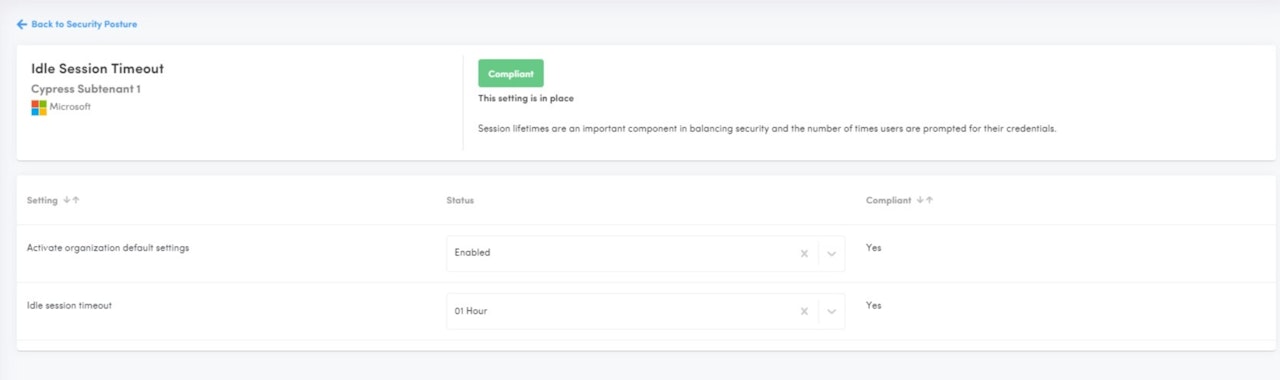
Idle Session Timeout
Description: Idle session timeout automatically signs out users from Microsoft 365 web apps after a set period of inactivity.
Why Use It?
Enhanced Security: Reduces the risk of unauthorized access to data.
Data Protection: Safeguards sensitive information when a device is left unattended.
Compliance: Helps meet regulatory requirements for session management.
Mitigates Risks: Lowers the chance of session hijacking.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: YES

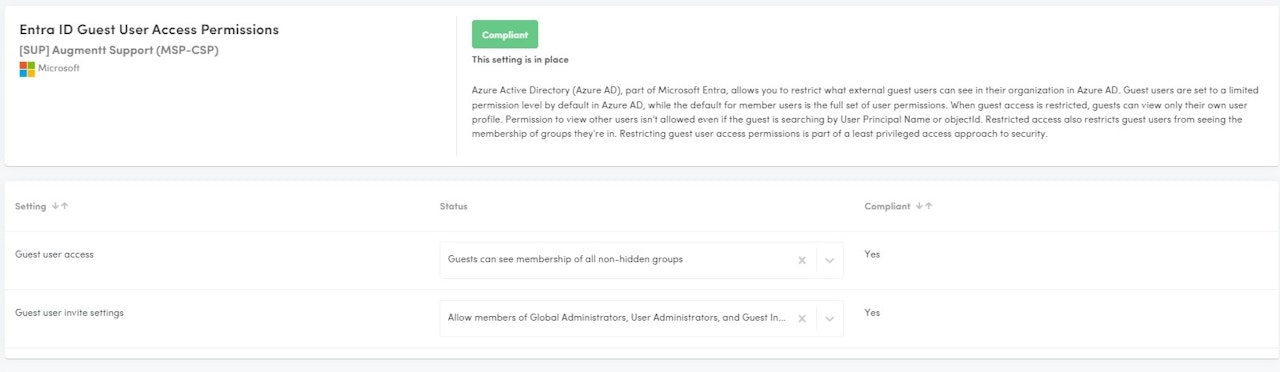
Entra ID Guest User Access Permissions
Description: Guest user access permissions in Entra ID manage what external users can access within your organization’s resources. This feature helps control the level of access granted to guests, ensuring that they have the necessary permissions without compromising security.
Why Use It?
Boost Security: Limits guest access to protect sensitive data.
Ensure Compliance: Meets regulatory and organizational standards.
Manage Access: Tailors permissions to fit collaboration needs.
How to be Compliant?
Guest user access, select either:
Guests can see membership of all non-hidden groups
Guests can't see membership of any groups
Guest user invite settings, select either:
Prevent everyone, including admins, from inviting external users.
Allow members of Global Administrators, User Administrators, and Guest Inviter roles to invite external users.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: No

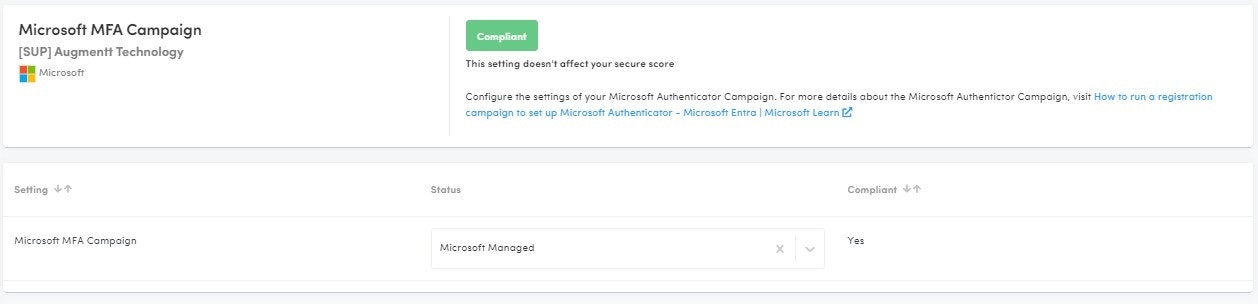
Microsoft MFA Campaign
Description: A registration campaign in Microsoft Azure AD is a feature that enables administrators to encourage or require users to register for Azure Multi-Factor Authentication (MFA) and self-service password reset (SSPR) in a phased rollout, allowing for a gradual transition to more secure authentication methods.
Why: This campaign enables administrators to specify which users are prompted to register, customize the registration experience, and set a deadline for registration, ensuring that users are adequately prepared and informed throughout the process.
Compliant: Enabled or Microsoft Managed
Not Compliant: Disabled
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: No

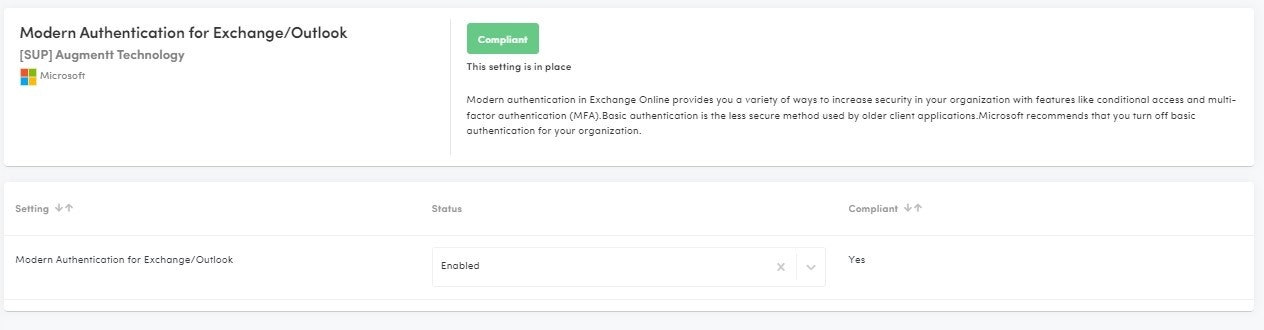
Modern Authentication for Exchange/Outlook
Description: Modern authentication in Exchange Online provides you with a variety of ways to increase security in your organization with features like conditional access and multi-factor authentication (MFA).
Why: Basic authentication is the less secure method used by older client applications. Microsoft recommends that you turn off basic authentication for your organization.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: YES

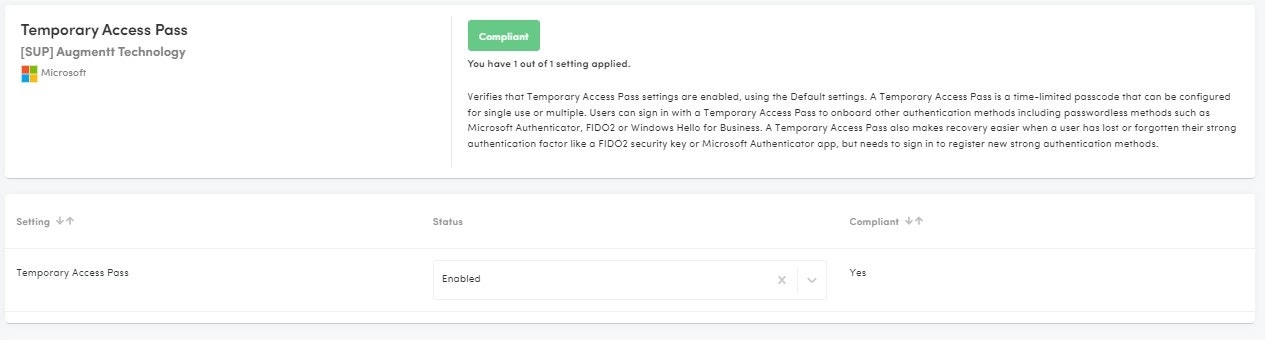
Temporary Access Pass
Description: This posture check verifies that Temporary Access Pass settings are enabled, using the Default settings.
Why: A Temporary Access Pass is a time-limited passcode that can be configured for single use or multiple. Users can sign in with a Temporary Access Pass to onboard other authentication methods including passwordless methods such as Microsoft Authenticator, FIDO2 or Windows Hello for Business. A Temporary Access Pass also makes recovery easier when a user has lost or forgotten their strong authentication factor like a FIDO2 security key or Microsoft Authenticator app, but needs to sign in to register new strong authentication methods.
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: No

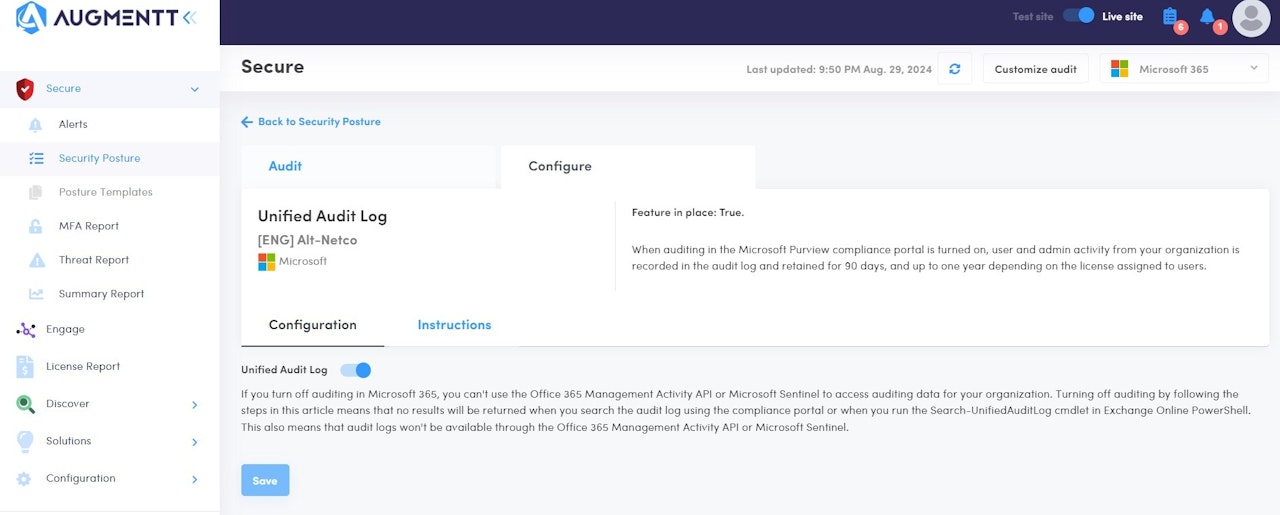
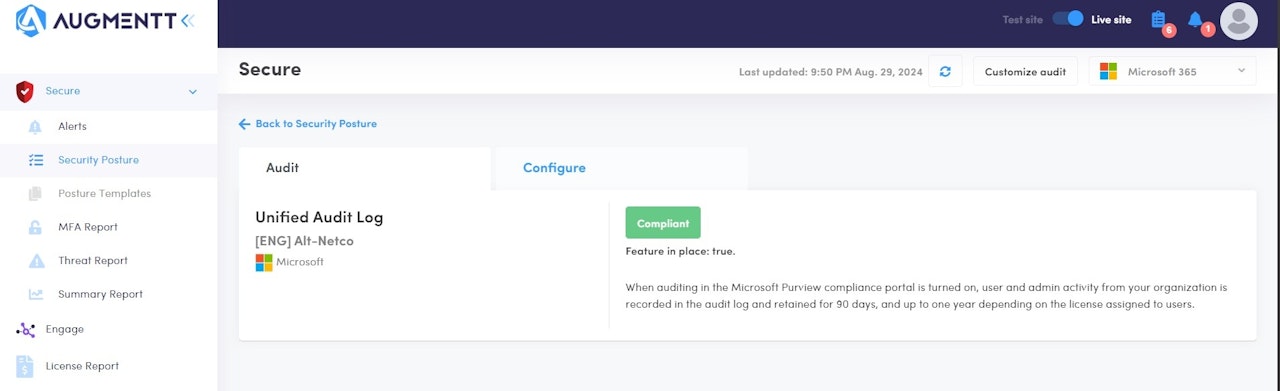
Unified Audit Log
Description: When auditing in the Microsoft Purview compliance portal is turned on, user and admin activity from your organization is recorded in the audit log and retained for 90 days, and up to one year depending on the license assigned to users.
Why: Unified Audit Logs in Microsoft Purview provide a centralized and comprehensive record of user and administrative activities across Microsoft 365 services, capturing thousands of operations daily. This centralized logging is crucial for security as it enables organizations to monitor, investigate, and respond to potential security incidents effectively. By retaining detailed logs of activities, organizations can conduct forensic investigations to determine the scope of a compromise, identify malicious actions, and ensure compliance with regulatory requirements. The ability to search and analyze these logs helps in detecting anomalies, understanding user behavior, and enhancing overall security posture by providing visibility into actions that could indicate security threats
Microsoft Licensing: Works with Basic licensing
Secure Score Impact: YES